Enabling Edge Workspaces on Windows 11 with Microsoft Intune

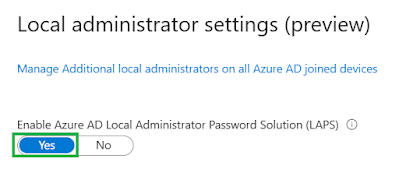
Présentation Edge Workspaces provides an incredible way for customers to organize their browsing tasks into dedicated windows. Each Edge Workspace contains its own sets of tabs and favorites, all created and curated by the user and their collaborators. Edge Workspaces are automatically saved and kept up to date. Workspaces are accessible anywhere customers use Microsoft Edge with their Microsoft Entra accounts. Prérequisites Users must have a Microsoft Entra tenant and Microsoft Edge version 114 or later installed or Microsoft Edge for Business version 116 To manage via group policy, Admins must have Microsoft Edge version 114 or later installed and version 114 of the policy files. Users must have access to a OneDrive for Business license to create an Edge Workspace Enable feature with Microsoft Intune Go to intune.microsoft.com Select Devices / Windows / Configuration Profiles and click Create Create profile Platform : Windows 10 and later Profile type : Settings catalog Compl...